Website reinfections are a serious problem for website owners, and it can often be difficult to determine the cause behind the reinfection — especially if you lack access to necessary logs, which is usually the case for shared hosting services.
Some of the more common causes of reinfections are issues like cross- site contamination or unpatched website software security vulnerabilities that get re-exploited. In this post, I’ll share with you a different method: how attackers can reinfect your website files in under a second by having a single malicious process running on the web server.
How It Works
Translated from Mandarin
This malware is primarily focused on “locking” existing files that are already infected, which prevents the website owner from being able to clean them infected files. From the tool, attackers can select different functionalities labeled as:
- Check the Environment
- Lock File
- Make locked files modifiable
- View Function
- phpinfo
- php_version
These functions are responsible for executing specific actions within the site. For instance, Check the Environment will list the path of php and the current PHP version. View Function is another handy feature which checks the PHP configuration information (e.g phpinfo) for disable_functions to give attackers an idea as to which functions are accessible and can (or cannot) be used to their advantage.
The disable_functions listing from phpinfo()
The function responsible for handling and creating a background process is Lock File. Once selected, this function targets a predefined file and it works as a persistent attack to prevent losing unauthorized access to the site if the website owner tries to remove existing backdoors.
Background Process Execution
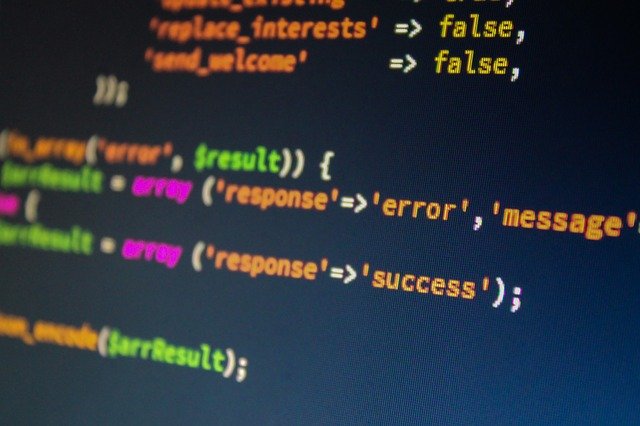
When the attacker submits a HTTP request containing ?action=lock to the PHP script, the malicious process is spawned using the function exec (assigned to the custom function run in the malware’s code).
case 'lock':
$php_path = getPhpPath();
if (functionCheck() !== false) {
$data_array['执行�'�令'] = "nohup $php_path " . $current_file_path . " >/dev/null 2>&1 &";
.......Source: https://securityboulevard.com/2020/09/the-hidden-php-malware-that-reinfects-cleaned-files/